The Cyber-Security War
For those of you who don’t know yet, the world is currently engaged in a massive global technological war over access to everything stored online. On one side we have regular internet users (or targets), who consist of large corporations, governments, small businesses and consumers like us all. On the other side we have the anonymous cyber-criminals (or hackers) who are intent on stealing all our online assets and confidential information for their own nefarious purposes. This war started in the mid-90’s with the creation of the internet and has now spread to every corner of the globe that the internet touches. Unfortunately the growth of the internet has corresponded to an even larger growth in cyber-crime and it is now the hackers who hold a massive and unfair advantage. As with all wars, the cyber-war will ultimately be won on strategy and resources. It is obvious that we desperately need new strategies and resources to reverse the current course of the war in our favor. However we should first ask ourselves if this cyber-war is actually winnable? And if not then what are the consequences and stakes for us as losers? And if the war is winnable how can we achieve this seemingly unlikely scenario?
Scope of the War
In this modern digital age all of our important financial, technical, business and personal information is increasingly being stored on a plethora of online servers around the world. With growing use of cloud and mobile services we have never been more exposed and vulnerable to online hacking. Conversely hackers have never been so powerful, organized, well-funded and dangerous. The ever-growing consumer demand for fast, convenient access to internet data from anywhere in the world is now playing into the hands of the hackers. In fact there is now very little confidential or personal data anywhere in the world that is inaccessible via the internet.
In 2014 cyber-criminals stole more than US $110 billion in currency funds and credit card fraud alone[latex]^1[/latex]. Moreover they caused in excess of $440 billion in ongoing damages and liabilities via trade / IP theft[latex]^2[/latex]. Although the main targets are large enterprises, governments, major retailers and banks it is consumers who ultimately pay much of the damages via higher pricing and additional fees (average ~ $300 per year). Furthermore identity theft is becoming a major problem for all consumers facing a battery of malware, viruses, worms, phishes and spyware every day. Ultimately all personal data is at stake and it is simply a matter of time until we all get affected by cyber-crime in some signficant way. This is now a $0.5 trillion problem that affects everyone.
The Major Casualties
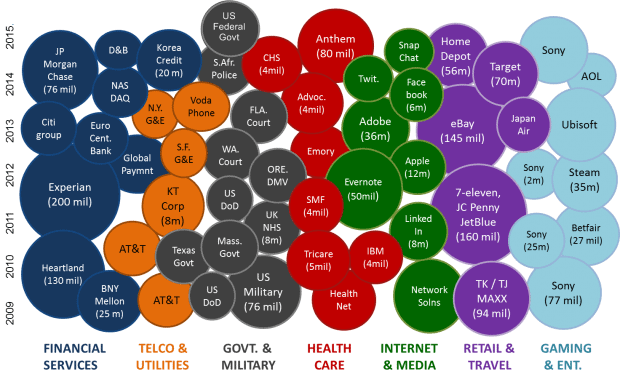
It takes just one successful breach into the internal server network of a large business or government organization to sieze hundreds of millions of personal records, usernames, passwords and credit card data. The litany of enterprises who have become repeated casualties in this war stretches across all global industries and international markets. However the majority of targets can be classified into eight industry classes; namely Financial Services, Telecom & Utilities, Government & Military, Healthcare, Internet & Media, Gaming & Entertainment, Travel & Hospitality and Consumer Retail (see graphic below). Despite numerous attacks against large retail brands such as Sony, eBay and Target, the potentially biggest and most profitable targets for hackers are Financial Services and Internet Services industries. These industries store the largest amounts of financial data online and have the largest customer bases.
Recent Large Enterprise Casualties[latex]^3[/latex]
(including no. of stolen records if given)
Of particular interest as a hacker target is the rapidly growing cloud data storage industry. Cloud storage providers not only store the personal and financial details of hundreds of millions of consumers, but also the confidential documents of millions of individuals, businesses and organizations. Consequently it comes as no surprise that cloud services from Apple, Google, Amazon and Dropbox have all been repeatedly hacked over the past few years. Moreover future attacks against cloud storage and software-as-a-service (SaaS) providers can be expected to increase as the cloud continues to permeate both consumer and business markets. Outsourcing data storage to the cloud ultimately means relying on the data security of cloud service providers.
The Major Culprits
The biggest problem with the cyber-war is that it is highly asymmetric and one directional in nature. It only takes a very small group of well organized and funded hackers to successfully breach and steal data from the largest enterprise networks in the world, and potentially steal billions of personal records and untold volumes of confidential data. The resources required to launch a sophisticated attack are much less than the resources required to defend against the attack. There is little downside for the attacker with most hacker groups operating under the protection of political regimes outside the juristictional realm of most targets in capitalist nations.
Consequently cyber-crime has evolved into a geo-political game with an estimated 75% of corporate security breaches in the west originating from China, Russia and North Korea[latex]^4[/latex]. While these nations might protect their own citizens against foreign prosecution, the spectre of government funded hacking also looms as a likely culprit. The remaining 25% of enterprise security breaches originate from domestic sources in North America, Europe, Asia and Australia. While domestic hackers can incur massive legal penalties if caught, the actual risk of being identified and arrested by authorities remains minimal for well organized criminal groups. From the hackers point of view the online world is their oyster and they are operating from behind a dark curtain of anonymity. They are the silent unseen predators and the world is full of large, juicy, vulnerable prey.
Plight of the Prey
The most obvious targets of cyber-crime are the customer credit card details that all online businesses and major retailers store on their server networks. Credit card details alone are worth between $5 and $100 each on the black market depending on the age, type and volume of cards supplied[latex]^5[/latex]. Additional private information such as customer addresses, phone numbers, SSN’s, usernames and passwords are worth even more to identity thieves who can steal many thousands of dollars from every unsuspecting card holder. Of course the consumers and banks share the immediate monetary damages of any credit card fraud, much of which can get passed onto cyber-insurance companies. Moreover the cost to banks of replacing stolen credit cards runs to billions of dollars every year. Ultimately however, any business or retailer may be sued by banks, insurers and consumers for all stolen funds and ongoing damages resulting from a data security breach. As Target recently found out, banks can be very persistent in pursuing legal action against retail vendors who have experienced major security breaches of their customers data.
Because banks store many other types of financial accounts online (in addition to credit card accounts), sophisticated hackers who target banks can steal much more than just a card number worth $100 on the black market. Once inside a bank server they can very quickly access and transfer huge amounts of currency assets from any bank account to anonymous accounts in friendly foreign countries. The very recently discovered malware hack against over 100 global banks resulted in almost $1 billion being stolen by a single organized crime syndicate over a two year period. Attacks against international currency assets, global commodities and stock market share portfolios are now becoming common place (and often hidden by their victims). Consequently consumer and merchant banks carry the largest inherent liabilities to cyber-crime. Hence cyber-security and cyber-insurance expenses have now become major boardroom issues at all banks. The banking and financial services industries definitely have the most to lose if the hackers were to win the cyberwar at the end of the day. They also have the greatest incentive to fund new strategies and disruptive technologies in the war against the hackers. New online financial technologies must either solve or mitigate the online security issue if they are to reduce costs and streamline processes for both banks and consumers.
Of course this is only the monetary side of the damages that result from online security breaches. The much larger concern is the theft of trade secrets, intellectual property, employee information and other confidential data that exists on the servers of every large enterprise today. The recent Sony breach demonstrates how a single limited hack of highly sensitive corporate information can sabotage major product releases and corporate relationships causing hundreds of millions of dollars in damages. The damage to the brand name of any retail enterprise that gets hacked is almost immeasurable. In addition to massive corporate damages, cyber-theft of confidential material from government and military organizations has the potential to change domestic and foreign political policy, surrender technological advantages to political enemies, and maybe even start a real physical war. Perhaps it already has?
Despite most large enterprises spending tens of millions of dollars on security every year the hackers are still winning the war. Conventional security technologies use firewalls, encryption, usernames, passwords and biometrics to attempt to create hack-proof barriers that prevent hackers gaining access to critical stored data. Unfortunately no matter how sophisticated or hack-proof a security platform might claim to be, nothing is ever 100% hack-proof. The best hack-proof platforms on the market can effectively only provide 99.9999% prevention of external breaches. Over time security breaches are inevitable and once the hackers are inside they can gain complete access to all of our financial information and private data with ease.
Our existing strategies and tactics are simply not working and a paradigm shift in thinking about online security is desparately needed to win the war (or at least reach a comfortable stalemate). Our modern internet society is now in a highly precarious position and ultimately we have only two options: to concede defeat, surrender our privacy and pay ever increasing cyber-insurance premiums .….. or fight back with radically new strategies and tactics.
The Future of Online Security
The traditional practice of simply shielding online data with multiple defensive barriers and user authentication doors has now proven a highly fallible and incomplete strategy. However new security technologies based on innovative new strategies and tactics are now emerging. These new technologies make the fundamental assumption that the hackers will always defeat any hack-proof security measures and can easily get inside any online server. In general, these new security technologies can be categorized into four different classes of security platforms, namely;
Adaptive Platforms
The concept of adaptive platforms is to partition various payloads of data throughout an enterprise network or cloud-based storage platform and continually monitor for security breaches in real time. Once a breach has been detected and identified the platform adapts its security protocols and locks sections down to isolate and limit the scope of the breach within the network. Companies such as Cloud Passage and Tanium are developing fast adaptive strategies that are all about reducing the potential real-time damage of breaches by a factor 10-100 or more. If you can’t stop them you might as well give them as little data as possible once you know you have a problem.
Mobile Enterprise Platforms
The advent of mobile platforms as the preferred user interface for many employee applications within an enterprise network has exposed a huge gaping hole in online security. Mobile devices such as smartphones and tablets typically have very poor security and are a common first entrance point for many hackers, phishers and malware. Startups such as Bluebox, MobileIron and ThreatTrack are addressing enterprise security from a uniquely mobile perspective. The idea is to stop hackers at the initial pinprick of a breach instead of waiting to deal with major server breaches later (when it is already too late). Adaptive security strategies can also be integrated on a mobile end-point platform. The more difficult it is to hack into an iPhone the more protected the enterprise network remains overall.
Counter-Measure Platforms
Instead of simply mitigating the effects of hacking we can actually go on the attack and mess with the hackers. Using a strategy borrowed from the NSA and Pentagon, there are several large security players such as Ricoh and Kapersky Labs who are developing highly pro-active counter insurgency platforms that take the fight to the hackers. It’s all about identifying and locating your hacker in real time, and then giving him a data payload that corrupts, disables or incapacitates his own data storage or online platform. Not only does the hacker lose all his stolen data but he can lose his entire software hacking capabilities and be more easily located by authorities. This strategy is obviously all about offense and not defense. However it also requires significant resources and manpower to implement.
Hack-Safe Platforms
In what may be the most ambitious and complex of these emerging security technologies, hack-safe platforms don’t try to prevent data breaches….. or even limit them. They simply try to ensure that any data stolen is totally useless to the hacker. This strategy is based on the principle of eliminating the liability of the breach instead of preventing the breach itself. This requires a very granular level of data management such that data packets are converted to a dispersed encrypted hack-safe format (note that a 100% hack-safe platform is theoretically possible while 100% hack-proof is not). Storage hardware vendor Cleversafe and software security startup Cryptyk* are combining principles of dispersed cryptography with enterprise and cloud data storage technologies to ensure that any stolen data from external breaches is incomplete and indecipherable. No doubt more startups will emerge in this area as secure cloud services begin to penetrate enterprise storage markets. Ultimately, the reason that this technology may have the most potential is because it uses the cloud to improve security instead of reducing it. Nothing like turning a perceived weakness into technical strength!
Although all four emerging security technologies are still at an early stage of their development, there exists the glimmer of hope that one or more can turn the tide of the war. Most large enterprises should seriously consider investing in several of the aforementioned technologies as a matter of legal liability mitigation. No doubt an integrated multi-pronged approach that is compatible with existing security platforms will produce the best results for most large enterprise networks. A new paradigm in online security is emerging and we can only hope that these innovative efforts live up to their potential. Otherwise the future of the cyberwar looks very bleak indeed.
 Adam Weigold, CEO of Cryptyk, is a physicist, technologist, market analyst, business development specialist, author and digital currency evangelist. A start-up veteran for early stage technology businesses operating in C-level, directorial and advisory roles, holding over 20 years of technology innovation and business management experience building start-ups in photonics, industrial automation, telecom, defense, medical devices, medical services and financial services.
Adam Weigold, CEO of Cryptyk, is a physicist, technologist, market analyst, business development specialist, author and digital currency evangelist. A start-up veteran for early stage technology businesses operating in C-level, directorial and advisory roles, holding over 20 years of technology innovation and business management experience building start-ups in photonics, industrial automation, telecom, defense, medical devices, medical services and financial services.
References
1: Bloomberg, CNN Money, Forbes
2: Gartner Research, Markets & Markets
3: informationisbeautiful.net, DataBreaches.net, IdTheftCentre
4: German Alliance for Cyber Security (Jan 2015)
5: Nilsonreport.com
*Disclosure Statement: The author Adam Weigold is a director and shareholder of Cryptyk Inc.
(image credit: Georgia National Guard)