A report created by proponents of the Computer Misuse Act (CMA) reform hopes to provide policymakers considering changes to the law with clarity regarding the legitimacy and legality of some instances of unauthorized access to IT systems. According to the report, cybersecurity experts and professionals agree on these issues.
The parties achieved a consensus around Computer Misuse Act
For years, the CyberUp movement has demanded Computer Misuse Act reform. Since the law was passed in the early 1990s, when the IT industry was considerably different, there is now a lot of worry in the security community that its current wording essentially criminalizes the work of ethical hackers and security researchers.
Due to this, the group has been pushing for adding a statutory defense to the Computer Misuse Act since 2019. Although the government announced last year that it would start working on reforming the Computer Misuse Act, little has changed since then, except for a failed attempt in the Lords to include a statutory defense in the Product Security and Telecommunications Infrastructure (PSTI) Bill.
“The consensus outlined in the report published today shows how a statutory defense can operate in practice. Crucially, it highlights that it will not open up a ‘Wild West’ of cyber vigilantism. Instead, by reforming the Computer Misuse Act to make defensible the activities outlined in the report, the CyberUp Campaign argues the government can enable a swathe of benefits, including improved cyber resilience of the nation and its allies, and accelerated growth of the UK’s domestic cyber security sector,” the campaigners stated.
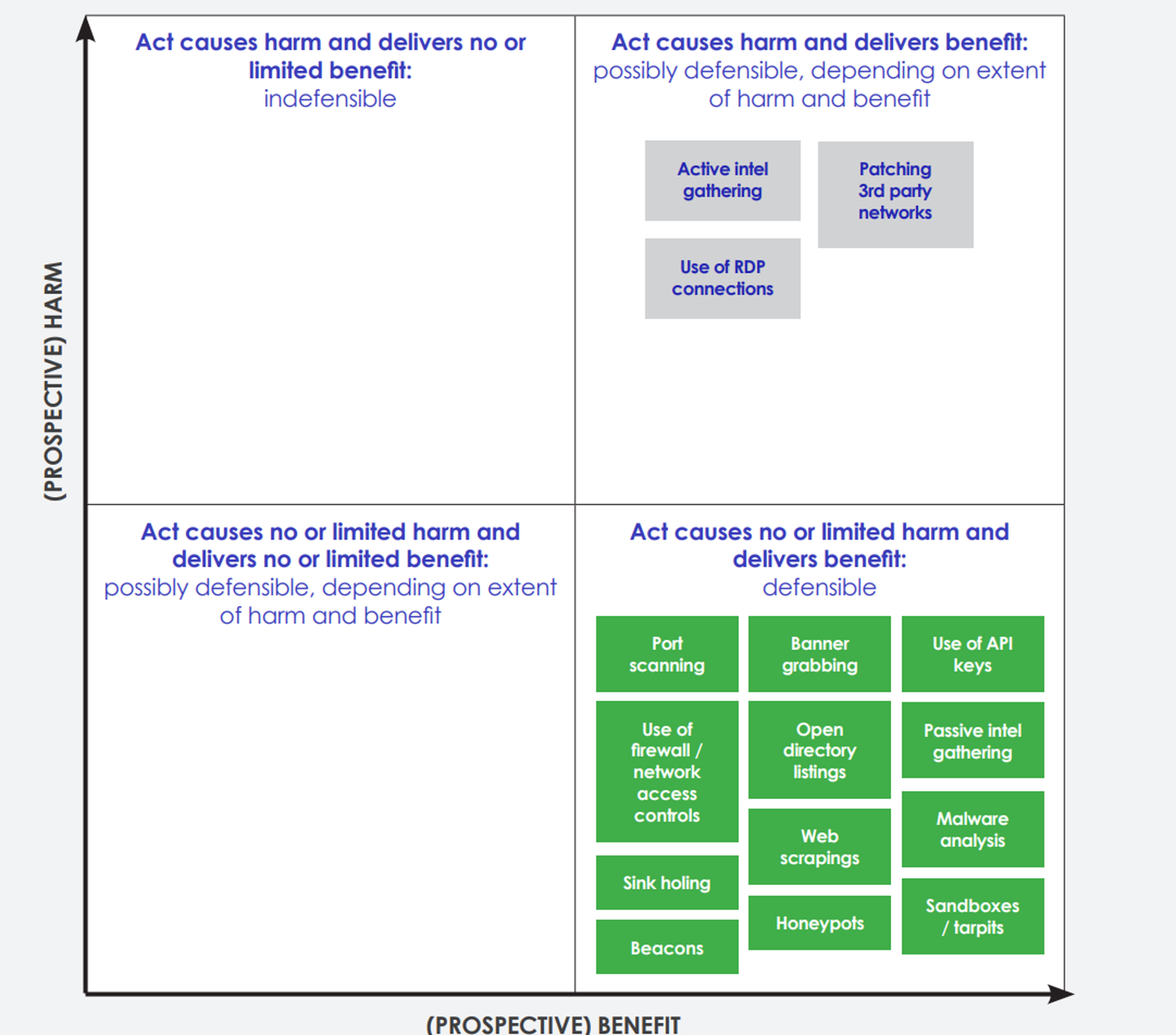
Survey participants were asked to classify cyber activities and techniques used in vulnerability and threat research into several categories: actions that cause no or little harm but deliver benefit, which may be defendable; actions that cause harm but deliver no or little benefit, which also may be defendable; and actions that cause harm but deliver no or little benefit, which are indefensible.
CyberUp agreed upon 13 activities that fall under the first category. These include using application programming interface (API) keys, banner grabbing, beacon use, implementing firewalls and network access controls, using honeypots and open directory listings, passive intelligence gathering, port scanning, using sandboxes or tarpits, destroying servers or botnets, sink-holing, web scraping, and malware analysis. CyberUp thinks the revamped Computer Misuse Act ought to make these acts justifiable as a result.
CyberUp discovered consensus in the second category, where forward or active intelligence gathering, patching third-party networks and using remote desktop protocol connections to gather information from attackers’ systems might be defendable, but further research will be required to determine how to manage them.
The next question asked respondents for their opinions on whether a newly created Computer Misuse Act should consider legitimate or illegitimate cyber activities and tactics that require unauthorized access.
The elephant in the room: Employees ignore cybersecurity training sessions
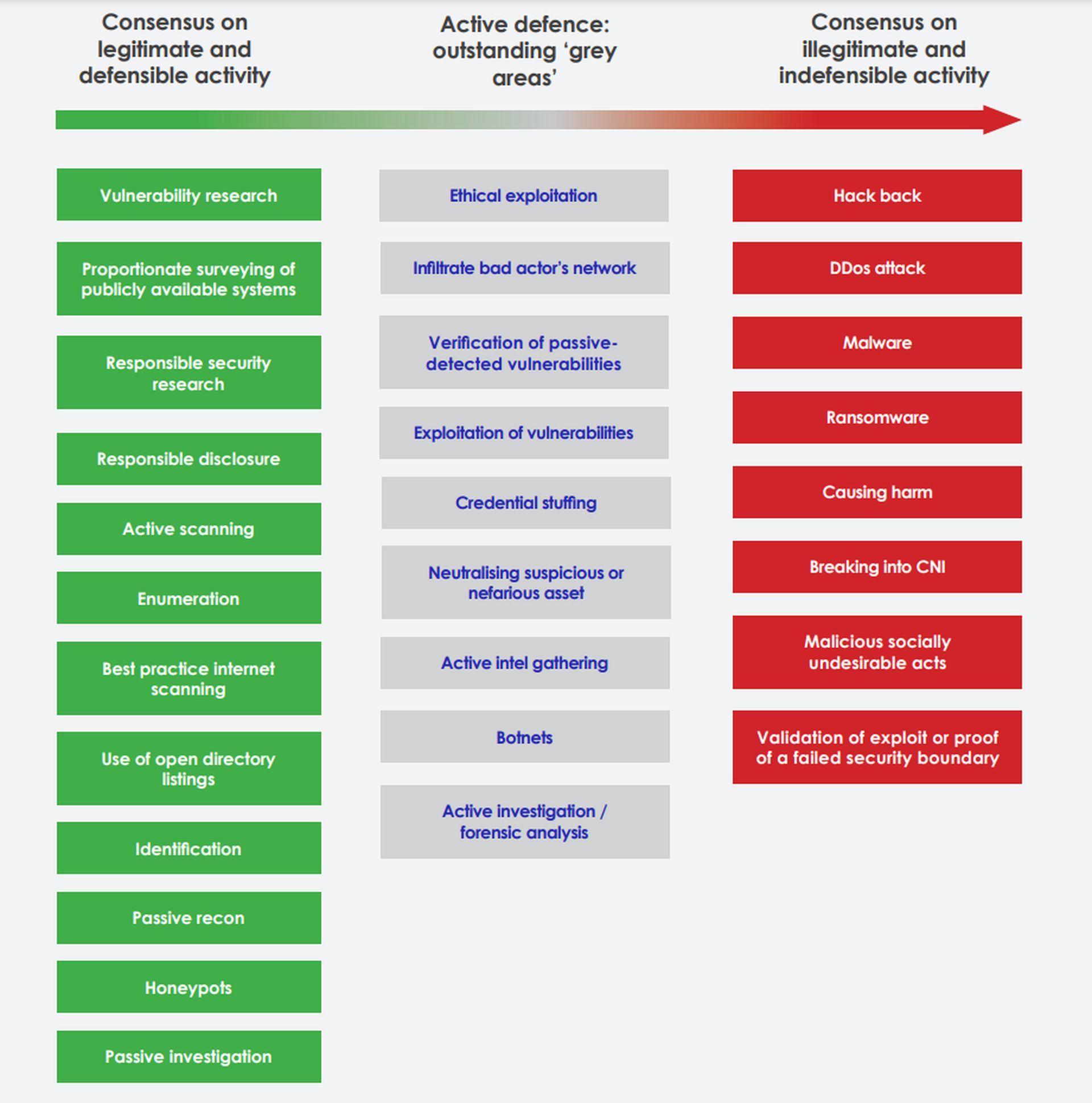
According to CyberUp, many activities can be considered valid cases of unauthorized access and should, therefore, be allowed. The surveying of publicly accessible (i.e., internet-exposed) systems proportionately for vulnerabilities, responsible security research, responsible disclosure, active scanning, enumeration, best practices for internet scanning, use of Active Directory listings, identification, passive reconnaissance and investigation, and the use of honeypots are some of these activities.

It was also discovered that there is consensus regarding what behaviors qualify as illegal unauthorized access, including hacking back, launching distributed denial-of-service attacks, using malware and ransomware, engaging in malicious “socially undesirable” acts, validating exploits, or providing evidence of a breached security boundary, and breaking into systems that are considered to be important pieces of the country’s critical infrastructure. The somewhat fuzzier idea of harming others is also included in this collection of acts.
The outcome
Finally, the research demonstrates an agreement that, as the Home Office is ready to move through with prospective regulatory changes, the group of cyber tactics referred to as active defense may still represent a gray area.
Actions like breaking into threat actors’ networks or systems, confirming passively detected vulnerabilities, exploiting vulnerabilities, credential stuffing, neutralizing suspicious or malicious assets, actively gathering intelligence, using botnets, and actively investigating and conducting forensic analysis are examples of these gray areas.
Rising cybersecurity risks threaten the healthcare industry
CyberUp emphasized that it is not necessarily suggesting that the entire list of actions included in its study find their way into government guidance accompanying a statutory defense because the list will undoubtedly become out-of-date given how quickly the security landscape is moving. Instead, it stated that it hoped a court would be able to use the level of agreement based on its “harm-benefit” matrix at any time while trying a fictitious future case.

It also discovered that several of its respondents disagreed with or had concerns about the general strategy of extending the boundaries of permissible activities. One person said that given the potential for “disruption of intelligence or law enforcement operations, diplomatic incidents or war,” the status quo should be maintained.
Cyberbullying is the digital version of our toxic behaviors, and no one needs that
Some respondents questioned whether there should be a licensing system for specific cyber operations, while another responded that only certified actors possessing valid court warrants should ever engage in these activities.

According to the results of this consultation process, there is agreement on the kinds of cybersecurity activities that require unauthorized access but are not controversial in terms of their potential to cause harm and should be legal under a revised Computer Misuse Act.
This agreement would be the cornerstone of a new legal framework for cyber security experts based on a statutory defense. This should reassure policymakers that a revised Computer Misuse Act won’t spark a cyber vigilantism wild west. Instead, it will make it possible for the UK’s cybersecurity sector to better safeguard the UK as part of the overall effort to secure society while ensuring that cybercriminals may be brought to justice.






