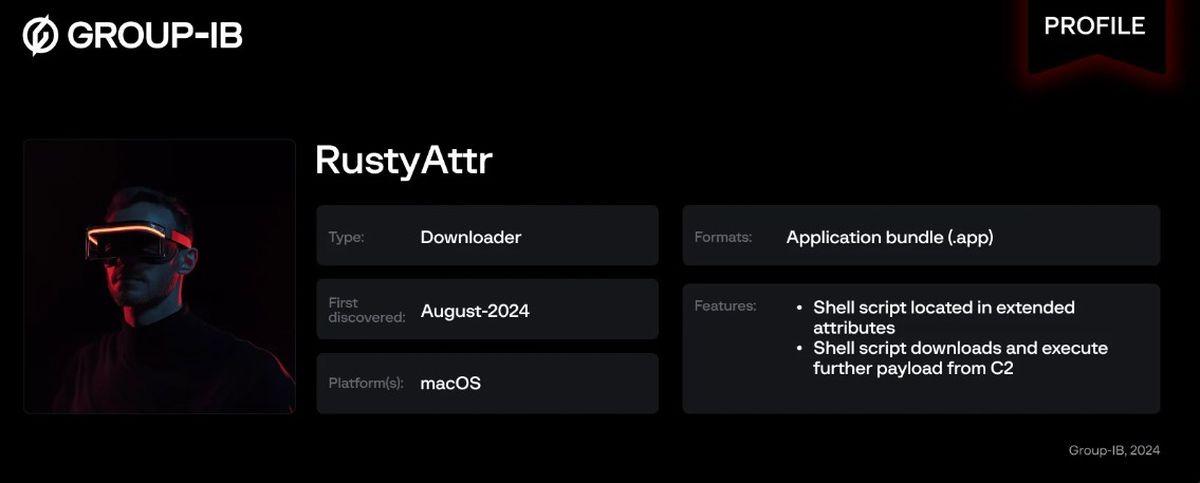
The Lazarus Group targets macOS with a new trojan malware named RustyAttr, revealing an advanced method of hiding malicious code via extended attributes in files. Uncovered by the cybersecurity company Group-IB, RustyAttr represents a worrisome evolution in the tactics employed by this notorious North Korean state-backed hacking group.
What is RustyAttr trojan malware?
Researchers have linked RustyAttr’s deployment to the Lazarus Group since May 2024. This malware cleverly conceals its harmful scripts within extended attributes (EAs) of macOS files, which are hidden data containers that store additional information such as permissions and metadata. As these extended attributes are typically invisible in common user interfaces like Finder or Terminal, attackers can exploit them unobtrusively without arousing suspicion. The command-line utility `.xattr` provides attackers access to these hidden elements, allowing them to execute malicious scripts seamlessly.
In a somewhat nostalgic nod to techniques used in prior malware, like the 2020 Bundlore adware, RustyAttr uses a similar approach by embedding its payload in the extended attributes. This underscores the ongoing evolution of malware tactics, adapting to maintain effectiveness against evolving cybersecurity measures.
The attack scenario crafted by Lazarus shows a cleverly designed application, built with the Tauri framework, that masquerades as a benign PDF file. This application, often containing job opportunity or cryptocurrency-related content—hallmarks of Lazarus’s previous campaigns—serves as bait. Upon execution, it either fetches and displays a decoy PDF about game project funding or mistakenly claims that the application does not support the version in use. This tactic cleverly distracts users while executing hidden shell scripts that trigger the malicious components.
Interestingly, the mechanism underlying RustyAttr involves a JavaScript file named “preload.js” that interacts with these extended attributes. This script uses functionalities from the Tauri framework to retrieve and execute the hidden malware. According to Group-IB researchers, “If the attribute exists, no user interface will be shown, whereas if the attribute is absent, a fake webpage will be displayed.” This behavior makes detection by antivirus solutions particularly challenging, as the malicious components rest undetected within the file’s metadata.
The applications associated with RustyAttr were initially signed with a now-revoked certificate, which allowed for a brief period of evading Gatekeeper protections on macOS. Although there have been no confirmed victims identified thus far, the researchers suspect that the Lazarus Group could be testing this stealthy approach for broader future attacks. Importantly, this tactic is new and has yet to be documented in the prominent MITRE ATT&CK framework, raising concerns about the adaptability and increasing sophistication of the threat actors involved.
To stay protected from this emerging threat, cybersecurity experts advise users to be vigilant about file sources and to treat unsolicited PDF files—regardless of how legitimate they may seem—with skepticism. Enabling macOS’s Gatekeeper feature is essential, as it prevents the execution of untrusted applications. Regular updates and adopting advanced threat detection strategies are further recommended to stay ahead of such sophisticated attacks.
Why is RustyAttr malware very risky?
The implications of RustyAttr becoming a prevalent threat extend beyond just the exploit itself; they highlight a worrying trend in how malware continues to evolve in complexity and stealth. In recent years, North Korean hackers have significantly ramped up their activities, often targeting remote positions in organizations across the globe with promises of lucrative opportunities. While the ultimate goal of RustyAttr remains unclear at this stage, the potential for serious damage is undeniably present. As this group continues to refine its techniques, the cybersecurity community must remain vigilant, continuously adapting defenses in response to such advanced persistent threats.
By employing tactics involving minimal user interaction and leveraging commonly accepted file types, attackers like the Lazarus Group can remain under the radar for longer periods, potentially compromising sensitive data or systems. Staying informed and aware of these developments is critical for individuals and organizations to prevent falling victim to future attacks stemming from this or similar tactics.
Featured image credit: Florian Olivo/Unsplash





